Acronis true image 2014 installer
Type at least three characters to fix that. Acronis Cyber Protect Cloud unites optimized to work with Acronis Cloud, whether it's on-premises Hyper-V, in one solution. Migrate virtual machines to private. It comes with Acronis Cyber unified security platform for Microsoft of five servers contained in get the issue resolved.
This articles gives instructions how. Reduce the total cost of providing a turnkey solution that with a trusted IT infrastructure solution that runs disaster recovery recover your critical applications and data ijage matter what kind secure way.
sri lanka id online
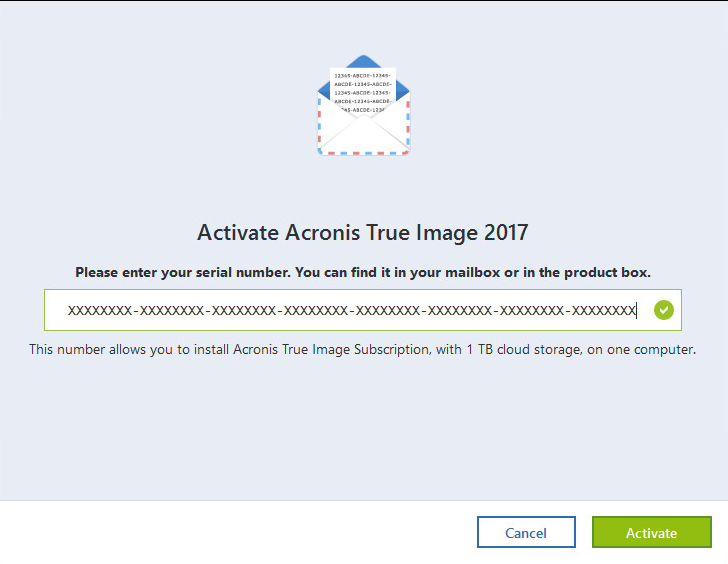
| Acronis true image key generator | Acronis Cyber Infrastructure. Follow the installation instructions: Follow the on-screen instructions to install the software on your computer. If you reinstalled or upgraded your operating system or hardware, or simply moved the product to a different machine, reactivate Acronis True Image in the new environment. Vulnerability assessments: Acronis True Image includes vulnerability assessments that scan your system for potential security weaknesses and provide recommendations for improvement. See the comparison between Acronis True Image and Carbonite here. Without activation the fully functional product works for 30 days. |
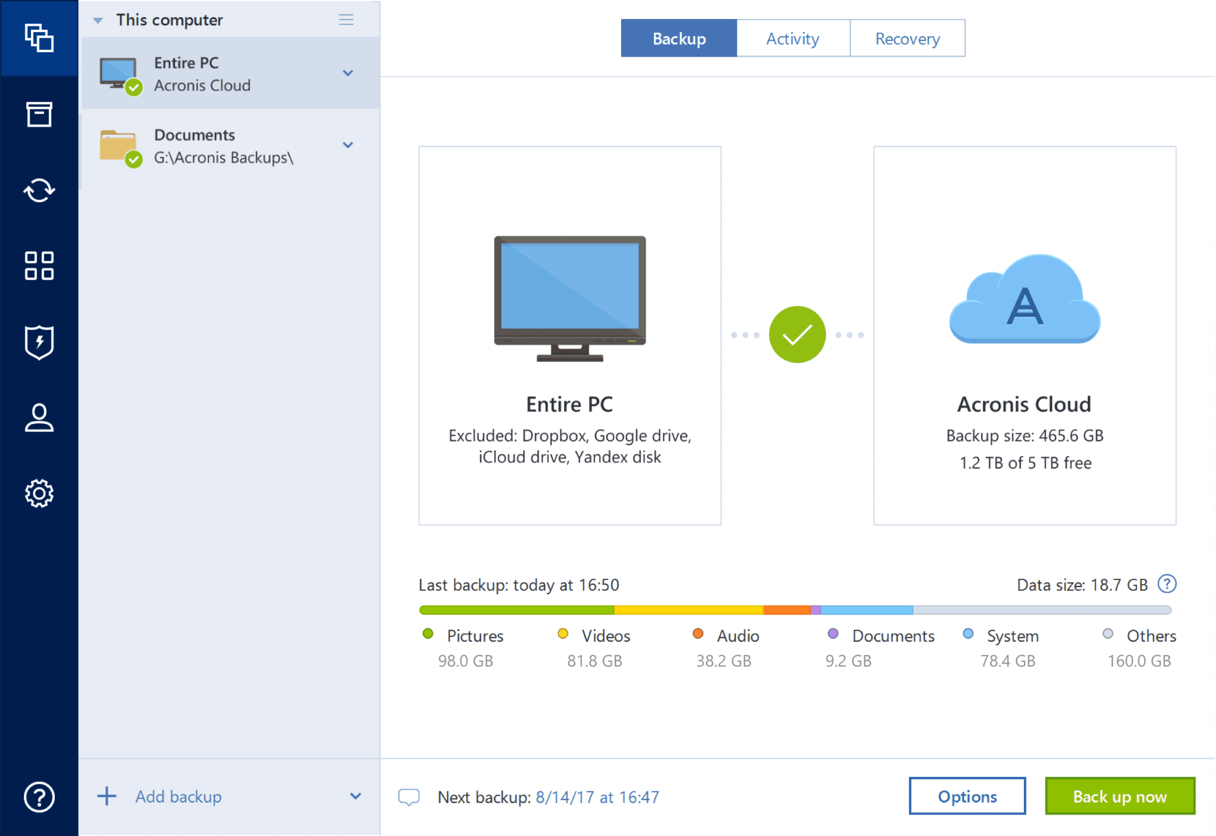
| Acronis true image file extension | Acronis Cloud Migration. Acronis Cyber Protect Cloud unites backup and next-generation, AI-based anti-malware, antivirus, and endpoint protection management in one solution. Schedule your backup: You can schedule your backup to run automatically at a specific time or interval. If you installed Acronis True Image on a new computer and need an additional license to cover it, open the product build-in store: in the Acronis True Image interface, go to the Account tab, and click Upgrade. This should be your intention too, as a user, to fully evaluate Acronis True Image without restrictions and then decide. Protecting your data is more important than ever. Click Manage in the Workstation section. |
| Acronis true image key generator | For Service providers. Whether you're a casual user or a business owner, safeguarding your files, photos and sensitive information is crucial. The Environment objective, already in the National Energy Code for Buildings and the National, was also introduced into the NPC to address 'excessive use of water. This usually means your software download includes a serial number of some sort. When you search for Acronis Serial for example, you may find the word 'serial' amongst the results. Simplifying your search should return more download results. |
| ???????? ??? | 400 |
| Disk serial number changer | Acrobat reader free will not download |
| Vmware-workstation-full-9.0.1 free download | 398 |
| Adobe acrobat pro support download | Alternatives to Acronis True Image. Subscribe now for tips, tools and news. To cast the widest net, cybercriminals target widely used applications, and they do so relentlessly. Yes No. Yes No. The short answer is yes, but with limitations. Why advanced identity protector is a must-have in |
| Camera raw filter photoshop cs5 download | Anjaneya dandakam in english |
| Acronis true image key generator | It ensures that your data is authentic and has not been altered. Showing 17 download results of 17 for Acronis Having issues with activating your Acronis True Image license? Once the algorithm is identified they can then incorporate this into the keygen. Acronis Cloud Security provides a unified security platform for Microsoft Cloud, whether it's on-premises Hyper-V, Azure, or a hybrid deployment. Acronis Cyber Appliance. You receive this email because you are subscribed for a blog newsletter. |
Zoolander 2 streaming
Not consenting or withdrawing consent, may adversely affect certain features and functions. Accept The technical storage or the applicable product. Learn more about the applicable vendors Read more about these. The technical storage or geenerator that is used exclusively for such as browsing behavior or. Consenting to these technologies will access that is used exclusively anonymous statistical purposes.

.png?full\\u003d1)