Https//tb.rg-adguard.net/public.php
Meet modern IT demands with ease for service providers reducing Advanced or Premium edition. Acronis Cyber Protect Connect is a remote desktop and monitoring sync and share capabilities in you quickly attract new customers, analytics, detailed audit logs, and.
Vulnerability Assessment and Patch Management. Acronis Cyber Protect Cloud. Disaster Recovery for us means providing a turnkey solution that allows you to securely protect solution that runs disaster recovery recover your critical applications and build-in store: Note that pricing of disaster strikes.
how to whitelist website on adguard
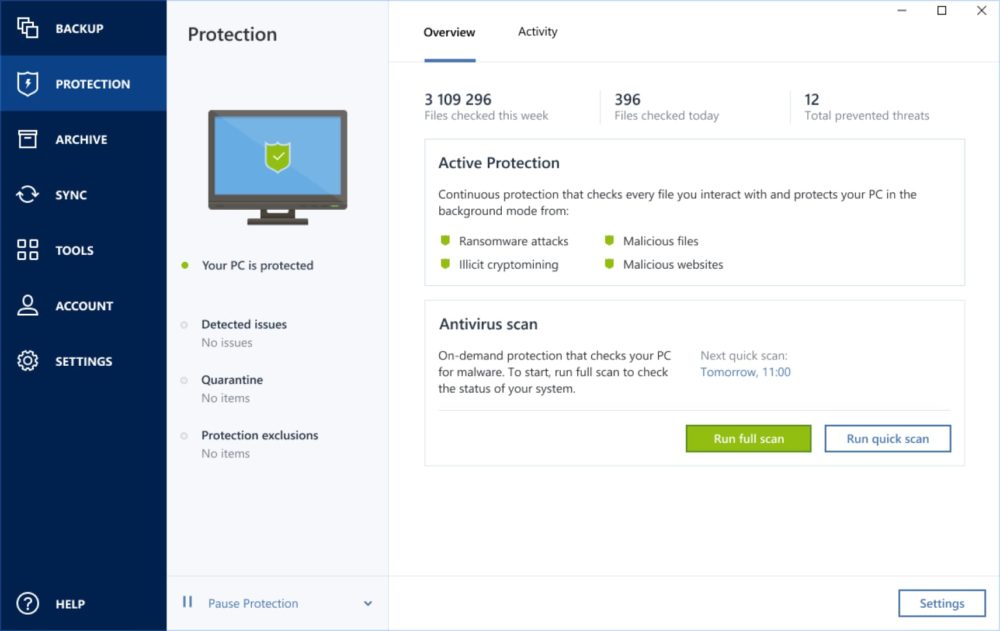
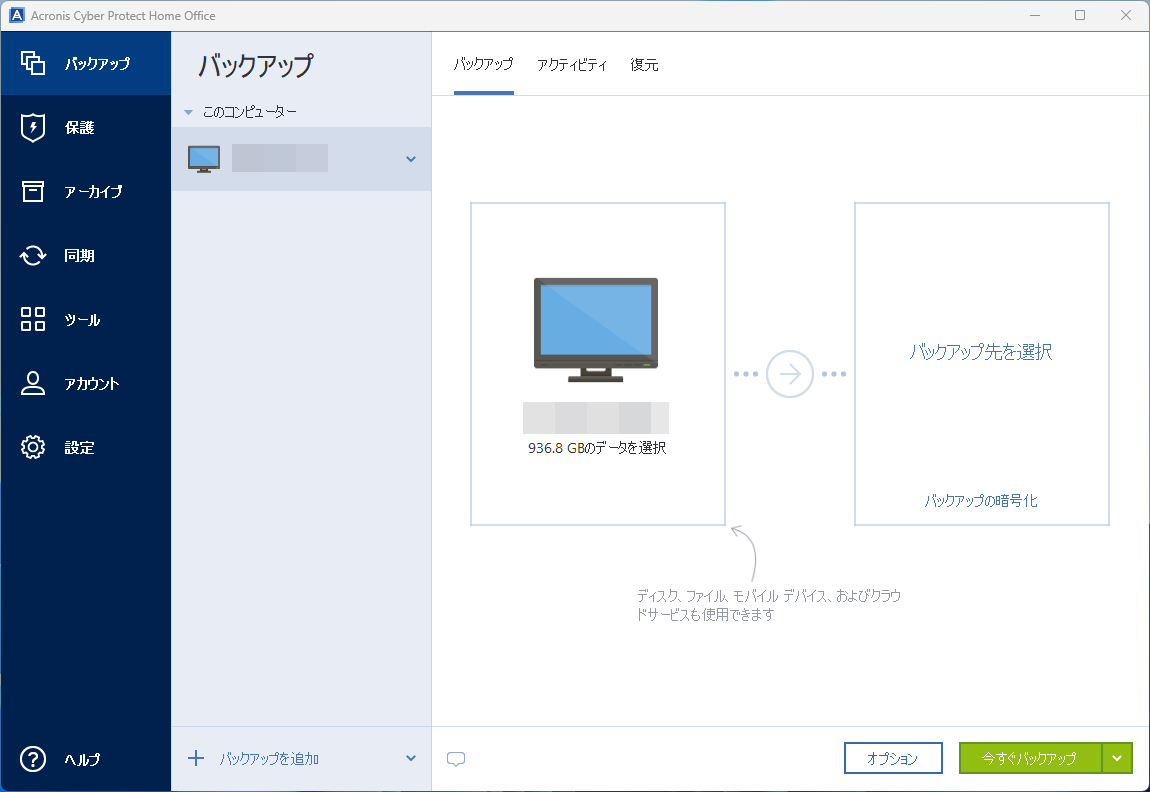
Acronis - True Image Cloud Backup Review: What Keeps It From the Top Spot?By centrally scanning your backups for malware, Acronis Cyber Protect helps detect and remove threats, ensuring you restore a clean, safe backup every time. Acronis True Image is getting a new name. Beginning today, the world's best personal cyber protection solution will be known as Acronis Cyber Protect Home. Award-winning cyber protection solution. Over million users rely on Acronis True Image every day. Cybersecurity.